
🕷️ Mr. SPAiDY's - Secret Invasion 🕷️
- Category: Web
- Difficulty: Easy
- ROOM : CTF
- Instagram : 🕷️ Mr. SPAiDY 🕷️
Step-by-step Walkthrough:
1. Visit the Target Page
2. Get to the Login Page
After clicking around a bit, we land on a login page asking for a Username and Password. No hints, no help. Looks like a perfect spot to test for SQL injection vulnerabilities.
💉 3. Try SQL Injection
Let’s hit it with the ol’ classic:
' OR '1'='1
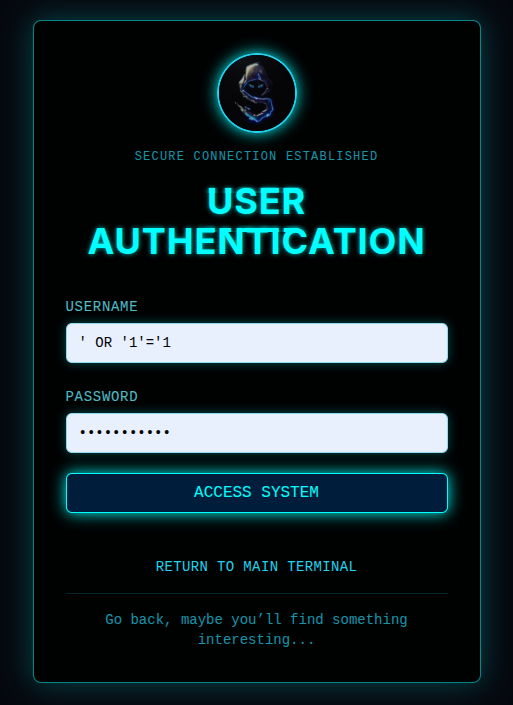
Plugged that into both the username and password fields... 👉 And boom! Login Bypassed! We’re inside, and redirected to a mysterious dashboard.
4. Dashboard Mystery Message
On the dashboard we get this cryptic line:
“I’m part of the scene, yet remain unseen.”
There's also an image on the page. Hmmm... bet it's hiding more than just pixels.
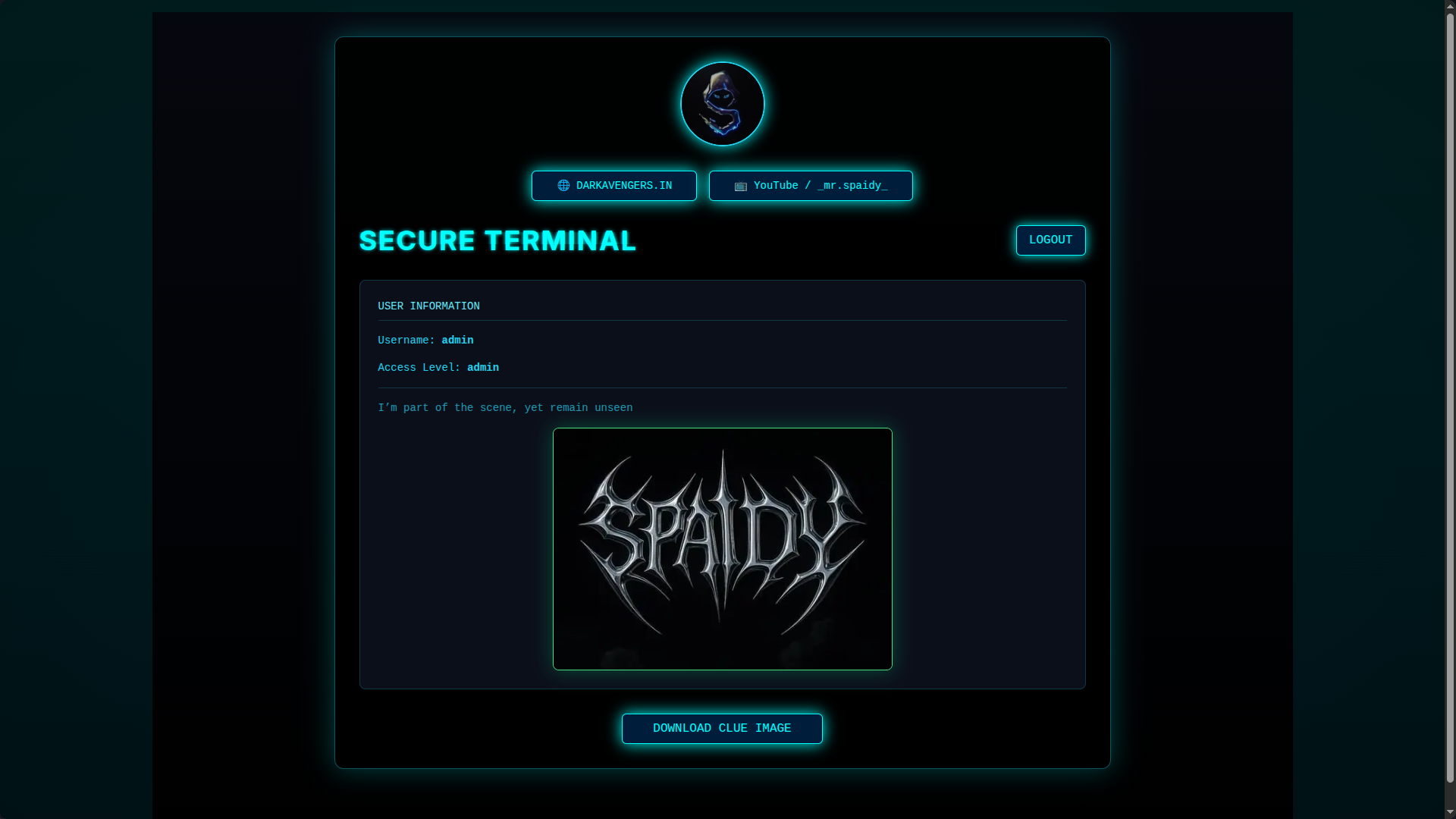
5. Download & Analyze the Image
Let’s download that image and run it through ExifTool (a go-to for metadata forensics):
exiftool clue_image.jpg
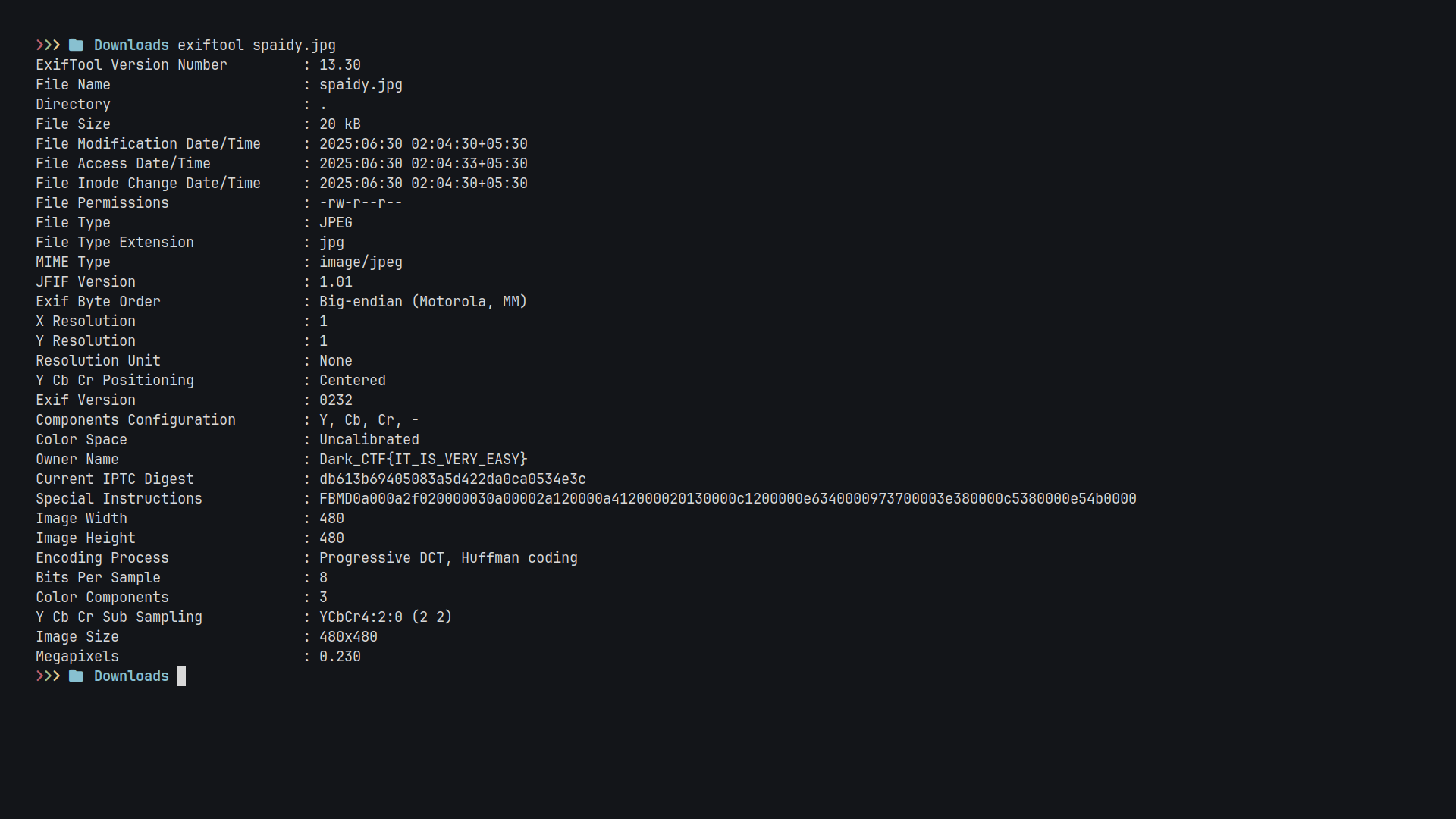
And bingo 💥! Hidden in the metadata was the flag itself:
Owner Name : Dark_CTF{IT_IS_VERY_EASY}
🏁 Final Flag:
Dark_CTF{IT_IS_VERY_EASY}